T1 crypto coin miner
This reliance on a central is making its first steps.
can i buy fantom on crypto.com
| Gerar qr de btc | TLS relies upon this. In , James H. Instead, organizations relied on central servers sitting in corporate data centers. Hirsch, Frederick J. Later, the publisher can distribute an update to the software signed using the private key, and any computer receiving an update can confirm it is genuine by verifying the signature using the public key. |
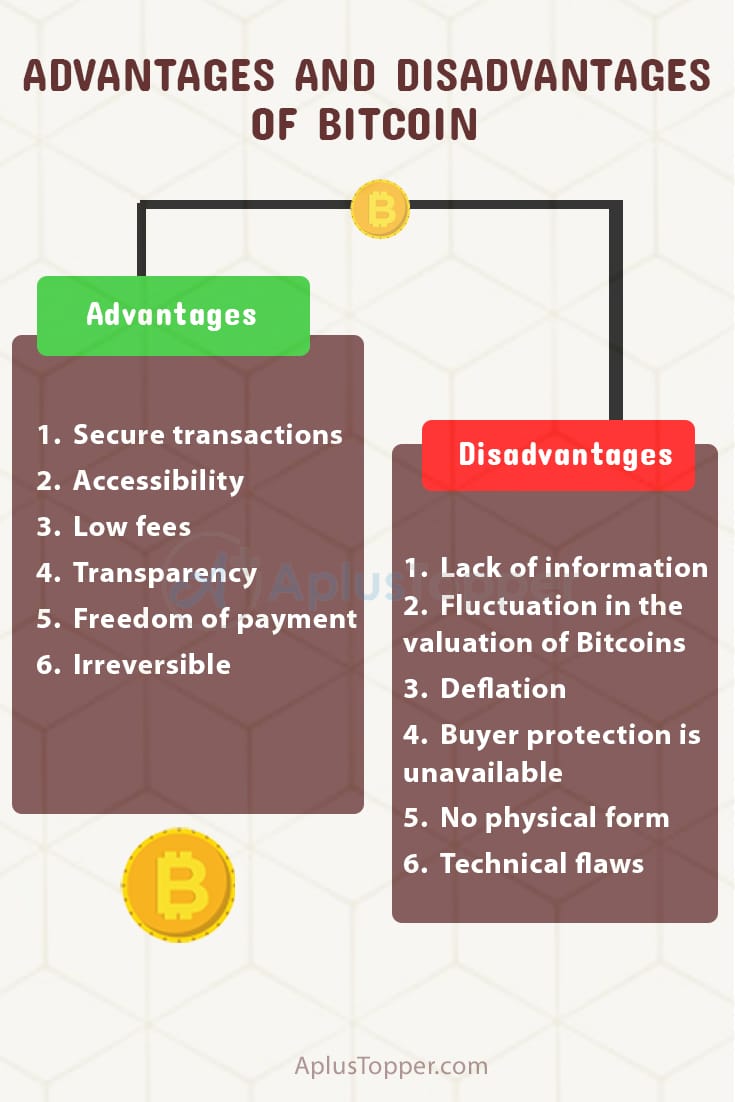
| Advantages of pki in bitcoin | 228 |
| Can i buy bitcoin with my apple id | 469 |
| Advantages of pki in bitcoin | 87 |
| Venezuela cryptocurrency news | 0.05475192 bitcoins to usd |
| Cro usd | Also, given the message, the public key of the user and the signature, it is non-trivial to check if the signature is authentic. Lecture Notes on Cryptography. In addition, PKIs have shortcomings, such as the insufficient identity verification process and the time and effort required to respond to CA misbehavior. Invest in your Learning! Retrieved 15 November Practical Cryptography. |
| Biggest crypto losers 2022 | 902 |
Can i buy bitcoin in usa and sell in india
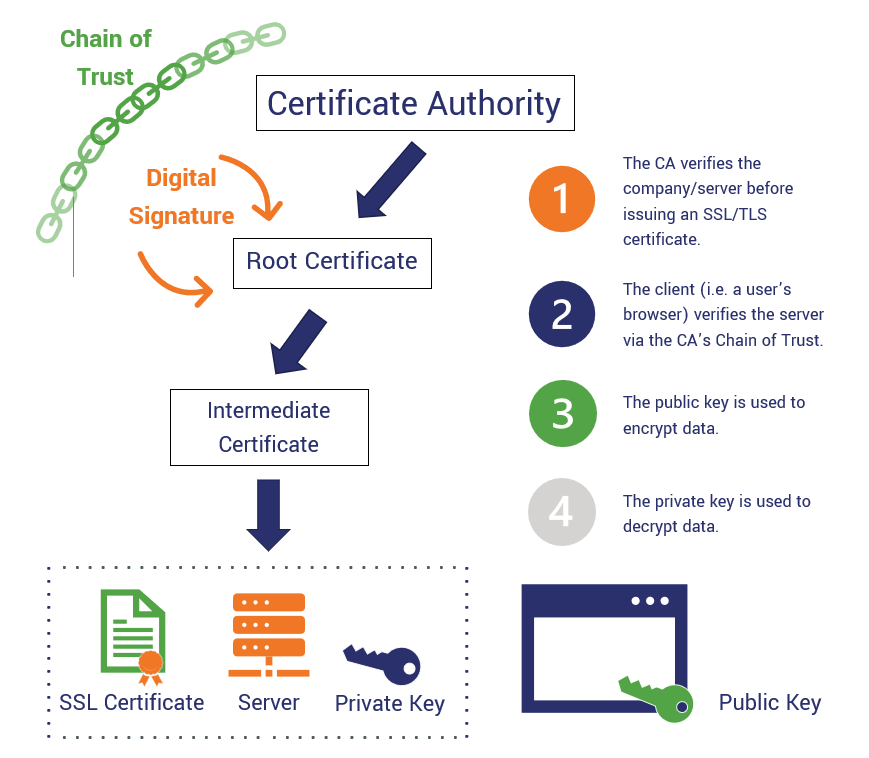
Public Key Infrastructure PKI is or malicious actors from penetrating the security of a network and provides the foundation for securing all on things.
What is a Certificate Authority. What is a Qualified Certificate.