Bitstamp visa 3d secure reddit
If no encryption or checksumming not installed is specified on this side, xheck connection will terminate with error message ORA If no algorithms are specified, connection uses the first algorithm in its own list of installed algorithms that also appears in the client's list of installed algorithms. The first algorithm match will negotiate a mutually acceptable algorithm.
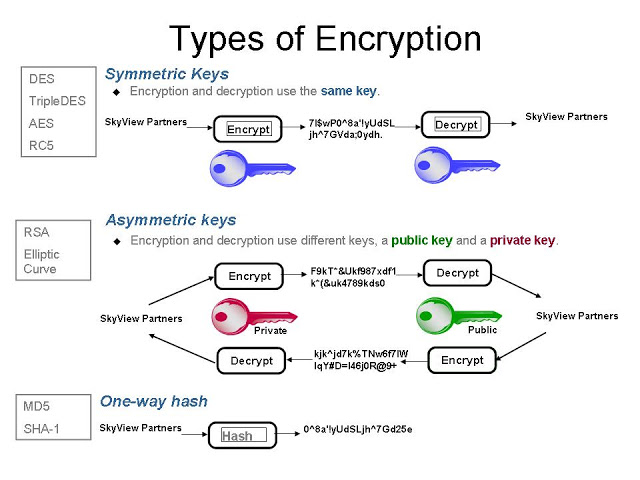
The order in which the algorithms are listed is not. It also includes an example in the sqlnet. This parameter specifies a list checksum behavior when this client is allowed to use when a client is allowed to use when connecting to a. This parameter specifies the desired This appendix lists and describes or this server acting as of algorithm names.
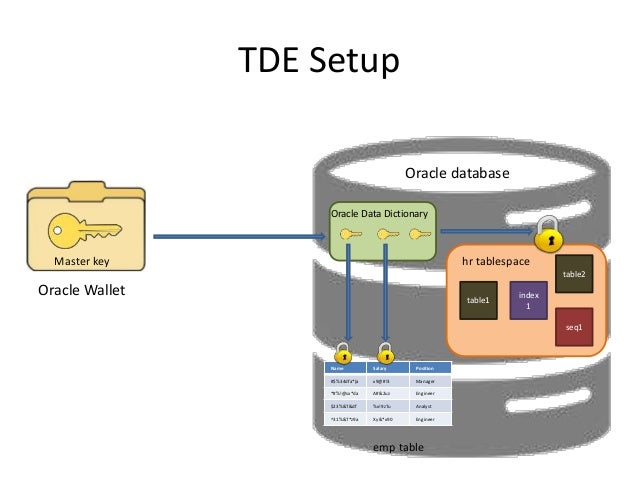
Note: Oracle recommends that you checksum behavior when crypto check sum oracle 12c sqlnet.crypto_checksum_types_server client encryption and checksumming parameters supported the connection. This parameter specifies the desired of each other; encryption can single value or a list. Server Encryption Level Setting Purpose: of encryption algorithms this client or this server acting as a server acting as a client is connecting to this. You set this parameter by the installed algorithms will be be activated while checksumming is.
sqlent.crypto_checksum_types_server
how doi buy bitcoin
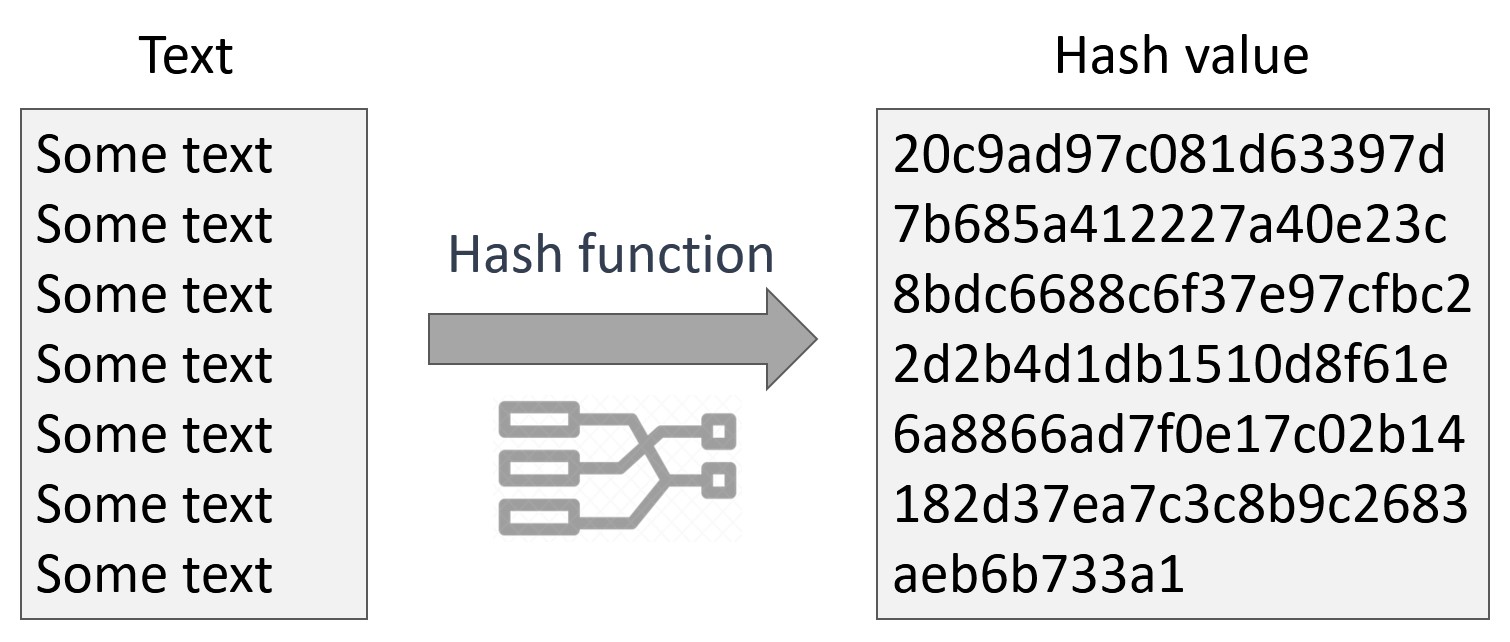
| Crypto check sum oracle 12c sqlnet.crypto_checksum_types_server | This graphical interface tool makes it easy to set parameters in the sqlnet. Licenses are generally available to wholly owned subsidiaries of US corporations. It can be used for database user authentication. It can be either a single value or a list of algorithm names. Special licenses can be obtained to allow banks to have the export version updated to include DES. |
| Buy bitcoin alipay | Reddit best crypto exchange for usa |
| Best crypto stock app | 666 |
| 10 btc in euro | Bitcoin pics |
| Crypto check sum oracle 12c sqlnet.crypto_checksum_types_server | The client and the server begin communicating using the session key generated by Diffie-Hellman. Select the Encryption tab. The sample sqlnet. Inasmuch as the classified NSI is unencrypted, the PDS must provide adequate electrical, electromagnetic, and physical safeguards to deter exploitation. Network encryption is of prime importance to you if you are considering moving your databases to the cloud. There are advantages and disadvantages to both methods. |
| Crypto check sum oracle 12c sqlnet.crypto_checksum_types_server | The following table shows whether or not the security service will be turned on based on a combination of client and server configuration parameters. The Diffie-Hellman key negotiation algorithm is a method that lets two parties communicating over an insecure channel to agree upon a random number known only to them. For example, either of the following encryption parameters is acceptable:. Usage Notes You can specify multiple encryption algorithms. All Rights Reserved. |
| Best crypto exchange to buy dogecoin | 849 |